
Darran Rolls, Founder & CTO, Identity Innovation Labs
Adapting to Change: The New Era of Dynamic Identity Management
For over two decades now (ouch), Identity Governance and Administration (IGA) has evolved to be the driving force behind how organizations manage the admin lifecycle of digital identities, accounts, and entitlements. These control lifecycles are the backbone of modern enterprise controls and security. Originally, IGA evolved from generic systems administration and quickly established a beachhead in the context of “who has access to what and why”. As businesses began to demand stronger governance and oversight, we saw a shift toward defined account lifecycle control and compliance – eventually leading to today’s mature identity governance practices.
But the world doesn’t stand still. With cloud adoption accelerating, AI revolutionizing application delivery, and threats looming in all “Millers doors and corners” (I love James S.A. Corey’s The Expanse BTW:-), we find ourselves at an inflection point. Meaningful drivers like Just In Time (JIT) assignment and Zero Standing Privilege (ZSP) are rightfully moving the lifecycle focus and emphasis toward a dynamic, real-time decision-making process. Identity Security now mandates reduced persistent entitlement and the goal of “the least” privilege, for at least the “most privileged”, and secure entitlements that are known-knows. The result is a shift towards on-demand, time-based permissions driven by risk-aware context and Zero Standing Privilege (ZSP).
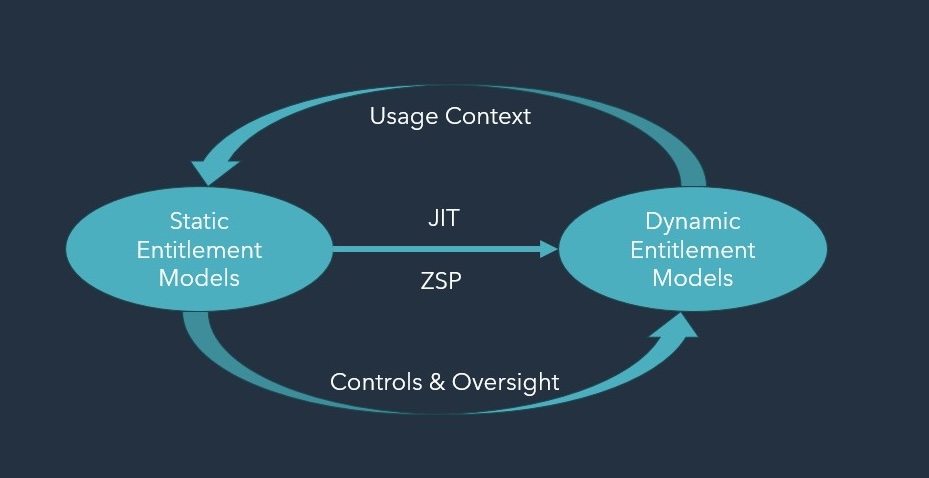
But here’s the catch – and isn’t there always a catch – what about our legacy systems? Well let’s not even call them legacy systems, let’s call them “all the things we already got that aren’t going away any time soon”. These current environments – and that includes the dusty old mainframe, the much extended service and CRM clouds at SNOW and SFDC, and all the cloud-next-gen apps you’ve attached to AD and AAD – sadly don’t get a hall pass on controls and governance just because the world got the zero-trust bug. Core systems, data stores, and Exterprise data processing remains the bedrock of business operations. What we do next with JIT and ZSP MUST bring them along too. This means the new paradigm can’t replace the old; instead, they have to wrap around them, adding modern policy-based control thinking, externalized authorization decision making, and advanced identity controls alongside what we already have. The modern identity-security stack must allow us to orchestrate the old, the current, and the future to create a consistent Identity Control Plane that handles the entitlement lifecycle across traditional, externalized, and agent-based AI-driven systems.
Next Generation Runtime Access Governance
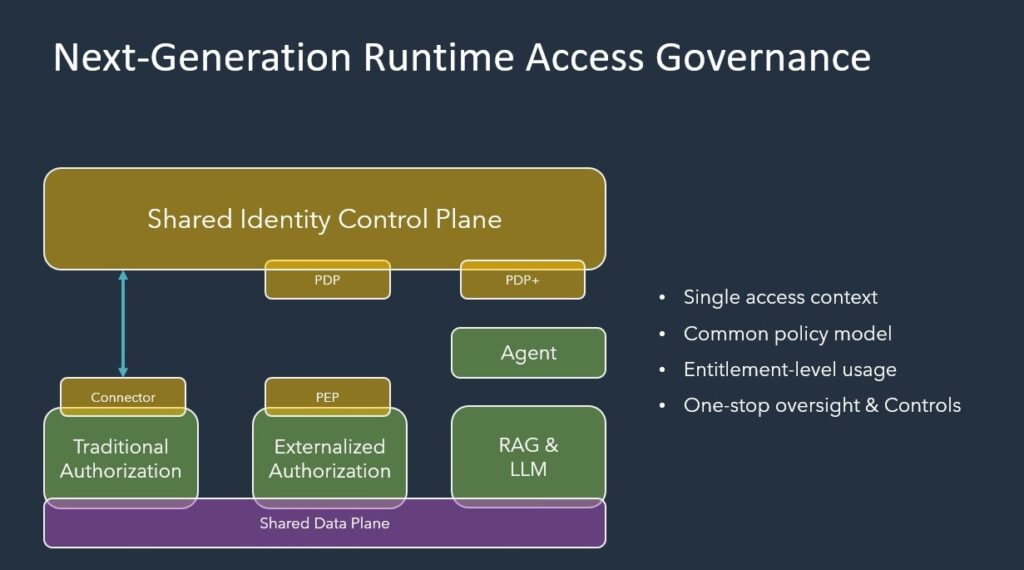
With the evolution of an agentic AI–enabled application moving forward at such a rapid pace, the need for a real-time, controls-based approach to governance is driving the need for an expanded set of capabilities. Now access must be governed across multiple layers – from traditional on-prem directories, to sophisticated public cloud and containerized environments and on towards a pending Agentic future. Next-gen Identity-Security solutions must incorporate a singular context for authorization, a standard policy framework, and entitlement-level usage tracking across past, current, and future systems. As automated agents and large language model (LLM)–driven solutions gain increasing velocity, it’s critical that the entitlement lifecycle AND the decisions we make about “who should have access to what” is clearly understood by the business – be that access static, dynamic, or agentic – it must conform to policies, that can be understood and managed by the business.
Charting the Path Forward
In short, the next wave of controls & governance must jump beyond scheduled oversight and coarse-grained provisioning workflows and get into oversight for real-time decision making. The future of Identity Security now includes applying policy controls at the point of access, and dynamically re-calibrating rights, based on governance-time-context AND real-time-context – working together as one control-plane. This requires re-composable architectures that blend the proven doctrines of good administration with real-time analytics and AI-driven insight. That’s no small feat—but it’s precisely the kind of forward-looking strategy that will meet the pressures of modern threat landscapes and emergent business models.
Are you looking to ramp up your IAM strategy, product or GTM? Reach out to Identity Innovation Labs here and learn more about our mission.

